I’m totally lame. Literally. I torqued my ankle a few days ago so I’m now couch-bound and glued to Cinemax HD watching the Star Wars marathon since they’re playing all six episodes back to back. I had grand plans to start installing the composite floor in the loft above the Trunkmonkey Racing garage but it doesn’t look like that will get started until tomorrow.
Blog
-
Happy Fricken November!

70°F. In Pelham, NH. On November 9th. With a forecast high of 63°F. Welcome to New England, people.
-
Round 7: Spammer vs. Barracuda…FIGHT!
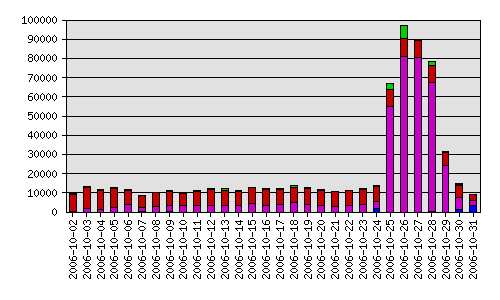
Just in case you’ve been keeping track, this is the seventh time a Spammer has forged one of the domains under my control as the return address of their Spam run. The first time it happened I felt shocked, angered, and betrayed. After I lost count of the incidents on my left hand and had to move on to my right hand to keep track it now just feels old-hat. Sure, it still pisses me off, but I now just chalk it up to being the owner of many high profile domain names.
Previously I noticed Spam runs immediately because the mail server started choking on the influx of bounces. This time the domain in question had a Barracuda Spam Firewall 200 sitting on the front lines in the DMZ; I didn’t notice the barrage until the midnight reports ran and I received the pretty pie charts showing a 600% increase in e-mail (and that was just the first day).
Days 2 and 3 jumped up to a 800% to 900% increase in e-mail before starting to plateau and drop off on Day 4. All in all around 350,000 bounces were blocked which is pretty routine for a forged run but the Barracuda performed without so much as a hiccup.
And, for the more visual among you, I’ve of course attached the obligatory pretty graph to show what a Spam forgery looks like. Green is legitimate e-mail, red is blocked Spam, magenta is bad recipient, and blue is rate control (too many connections).
-
Call out Gouranga be happy
Sometimes Spam makes me smile. Sometimes Spam is artistic. Sometimes Spam is almost Zen-like. And I’m especially amused when Spammers forget to include a link in their prose.
Call out Gouranga be happy
Gouranga Gouranga Gouranga!
That which brings the highest happiness -
Viral marketing secrets revealed!
Finally, someone reveals all the secrets of viral marketing in one single easy-to-read step!
-
The Litterbox has been re-launched
The Litterbox, one of my first domains, used to be a Web site dedicated to domestic pet rescue and care. After a few years of operation quite a few other sites like Petfinder.com popped up that did a much better job of what my wife Kelly and I were trying to accomplish as a hobby in our spare time. So we emptied The Litterbox six or seven years ago and it had been sitting collecting dust since then.
But what good is an empty litterbox? Litterboxes should be full! So a few days ago I filled The Litterbox back up with what else but cat pee. Enjoy.
-
naymz allows you to control your online identity
 naymz, a new online identity service, claims to allow you to control your online identity. The premise is that search engines may still be linking to incorrect, outdated, or embarrassing data. naymz allows you to create a profile that is “guaranteed” to be at the top of search engine results to help prospective employers and dates find the “real you” and to reconnect with old friends.
naymz, a new online identity service, claims to allow you to control your online identity. The premise is that search engines may still be linking to incorrect, outdated, or embarrassing data. naymz allows you to create a profile that is “guaranteed” to be at the top of search engine results to help prospective employers and dates find the “real you” and to reconnect with old friends. -
Add more Courier-IMAP connections under Plesk
By default, UNIX-based servers running Plesk and the Courier-IMAP e-mail server drastically limit the number of inbound connections to prevent users from opening up too many concurrent sessions. Unfortunately, this artificially-low restriction can impact legitimate users who have multiple computers connecting to the Courier-IMAP server from behind a firewall or a single computer that runs an IMAP client that takes advantage of mailbox caching.
Plesk comes configured with a limit of 4 connections per IP address and a limit of 40 connections total. Modern IMAP clients such as Mozilla Thunderbird use mailbox caching to open up multiple connections to increase performance. In the case of Thunderbird, it opens up 5 connections by default which is already 1 connection more than Courier-IMAP’s default restriction. Add another few family or corporate computers behind a firewall and those additional users won’t be able to connect at all since a single Thunderbird client is already utilizing all 4 connections.
To increase this restriction, modify the
/etc/courier-imap/imapdconfiguration file and changeMAXDAEMONSandMAXPERIPto a more sane number. In the case of my configuration, I changedMAXDAEMONSfrom 40 to 80 andMAXPERIPfrom 4 to 40. This allows all the machines behind my home firewall to connect to multiple accounts on the e-mail server with mailbox caching enabled.But even those numbers may be too low for a corporate colocated server that services an entire company. Tweak those numbers based on your employee base; if 50 employees are connecting to the e-mail server from behind the same firewall then
MAXPERIPcould need to go as high as 250 (50 employees times 5 cached mailbox connections). Add e-mail clients of people working from home andMAXDAEMONScould go as high as 300 or 400.Obviously, the connection limits are to prevent the Courier-IMAP server from using too many memory and CPU resources on the machine. Tweak the numbers based on the memory footprint of each daemon process and how much memory you have.
-
Careful with that FedEx account number
Taken from RISKS Digest 24.43:
Date: Wed, 20 Sep 2006 10:45:49 -0700
From: Matt Wilbur <[email protected]>
Subject: Careful with that Fedex account numberSending packages with Fedex is now easier than ever, thanks to the fedex.com website. Unfortunately, it’s too easy. In most cases, if you know a company’s account number, you can send whatever you like using the site, assuming you have a pulse, a browser, and access to the Internet.
We recently had an angry ex-employee use our account number to send multiple small dollar amount packages all over the place. The dollar value was too low for the authorities, and it was really just a nuisance. Our “Fedex
person” called Fedex to stop this, and customer service told her the only way was to change our account number. This would be painful, so we sent him letters telling him to stop. It didn’t. We called Fedex again, this time asking for security, using words/phrases like “fraud,” “theft,” and “you will have to pay when we reverse the charges.” We didn’t get anyone from Security, but they did begin to listen.After being bounced around at fedex, we learned the following:
Unless you take specific action (enable and configure Shipping Administration for your account within Ship Manager on the website), anyone on the planet can create a fedex.com account, associate it with your account number, and ship whatever, wherever they way, third party included.
there is no way, even with shipping administrator, within fedex.com, to view the logins associated with your account. We had to call and insist on a list – for “security” reasons they could not email or otherwise send us a list, but were able to tell us logins, names, last login, and email of active accounts.
After setting up Shipping Administration, we verified that this ex-employee (or anyone else we don’t approve) can no longer set up a new login and associate it with our account.
After about an hour on the phone, we were able to get his login deleted (and learn all of this additional information about their system).
Risks? For Fedex? Not defaulting to a more secure configuration (like, want to use fedex on the web? First sign-in associated with that fedex account must set up “Shipping Administrator” to prevent unauthorized use). Building an application with all the shipping capabilities imaginable available, and very little for the account holder to manage access and security. Not having a security contact or phone number listed, or accessible by calling in to customer service. Money lost to fraud by abuse of this system.
For the Fedex user? Giving your fedex account number to third parties who may ship things to you, unless you know and trust them, and trust their handling of your account number. Not watching your bills closely. Signing up and using for a service that, when you think about it, is far too easy to use to have any built-in safety.
-
August RedHat Enterprise fixes break Plesk DNS
The most recent batch of RedHat Enterprise (RHEL) fixes rolled out this past week break DNS (bind) on servers running Plesk. My Plesk 7.5.4 installation was effected as well as many other Plesk 7.x and 8.x users. The problem appears to be with a conflict between RedHat’s bind-chroot RPM and Plesk’s chroot system.
When the latest RHEL RPMs were rolled out the
/etc/named.confsymlink which should point at Plesk’s/var/named/run-root/etc/named.confconfig file was changed to point at RedHat’s default/var/named/chroot/etc/named.conffile. Post-install scripts then munged the location of the Plesk config files. This resulted in the following error when starting or restarting the nameserver:none:0: open: /etc/named.conf: file not foundA thread was started in the Plesk forums reporting the problem and a Rackspace employee replied in an earlier thread with a fix.
Basically,
rpm -e bind-chrootto remove the RedHat RPM that conflicts with Plesk and then re-symlink/etc/named.confto point back at the proper/var/named/run-root/etc/named.confconfig file. This drops Plesk’s config files back into place.